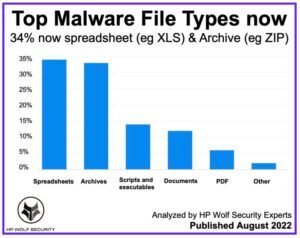
頂級惡意軟件文件類型 – 惠普狼安全 分析了最常見的惡意軟件文件類型,電子表格名列前茅.
新的調查報告顯示電子表格是最常見的惡意軟件文件類型 34% 和 11% 存檔中傳遞的威脅增加.
Wolf Security 提供全面的端點保護和彈性,從硬件級別開始並擴展到軟件和服務.
該報告回顧了顯著的威脅, HP Wolf Security 在日曆 Q2 的客戶遙測中發現的惡意軟件趨勢和技術 2022. 重點包括對 CVE-2022-30190 帶來的風險的分析, 影響 Microsoft 支持診斷工具的零日漏洞, 包括在利用此漏洞的攻擊者中看到的活動, 以及捷徑的興起 (LNK) 文件作為執行惡意軟件的無宏替代方案.